-

5 Best Ways to Run File Explorer as Administrator in Windows 11
File Explorer allows you to browse your computer’s internal and external drives, folders, and file types. If you are not using an Administrator account, the…
-
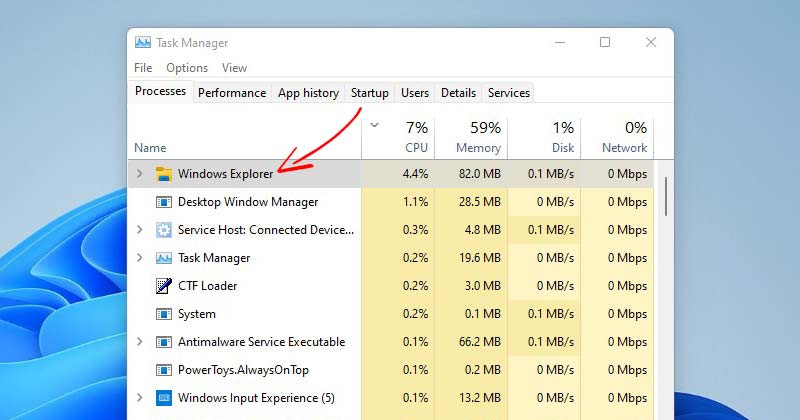
How to Restart Windows’s Explorer.exe to Fix Frozen Desktop Windows 11
Those who have been using Windows for a while may know that sometimes the operating system lags. Sometimes, the Start Menu, Taskbar, and other components…
-

5 Best Ways to Record Your Screen on Windows 11
By recording your screen in Windows 11, you can show off the new features you’re playing with or even record your gameplay. Whatever the reason,…
-
How to Turn Windows Efficiency Mode Off
If you’re using the Windows 11 22H2 build or even the very latest version of Windows 11, you will know about Efficiency Mode. What is…
-

How to Turn Off Windows Security for Chrome
Google Chrome users may know that the browser can authenticate users with Windows Hello to provide access to saved passwords. If you have set up…
-

How to Mount Folder as Drive in Windows 11
To mount a folder as a drive in Windows 11, you need to use the built-in subst command. The subst command is mostly used for…
-

How to Check Startup and Shutdown History in Windows 11
While using Windows 11, sometimes you may want to check your PC’s Startup and shutdown history. There could be various reasons you would like to…
-
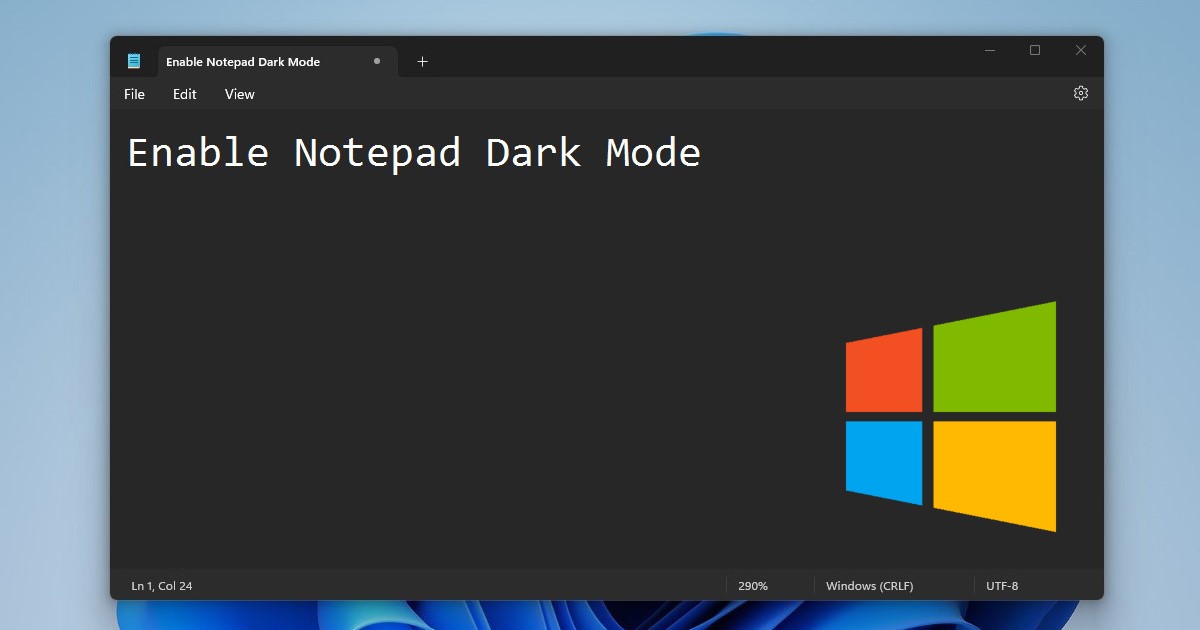
3 Best Ways to Enable Notepad Dark Mode on Windows
If your PC runs on Windows 11, you can enable dark mode on your Notepad. Actually, Notepad dark mode is also available for Windows 10,…
-

Windows 11 Delivers Built-In Security for Education and Beyond
Schools faced more ransomware attacks than hospitals or governments faced in 2023, according to research from Emsisoft. Districts were targeted more in 2023 than they…
-

Cybersecurity Pilot Program for Education Earns an ‘A’
Nation-state adversaries and cybercriminals continue to launch cyberattacks at an unmatched pace across all industries, and the education sector is in their crosshairs. Education is…